Sensitive data in email
Hjalti Magnússon
3. May 2024
security
privacy

Privacy
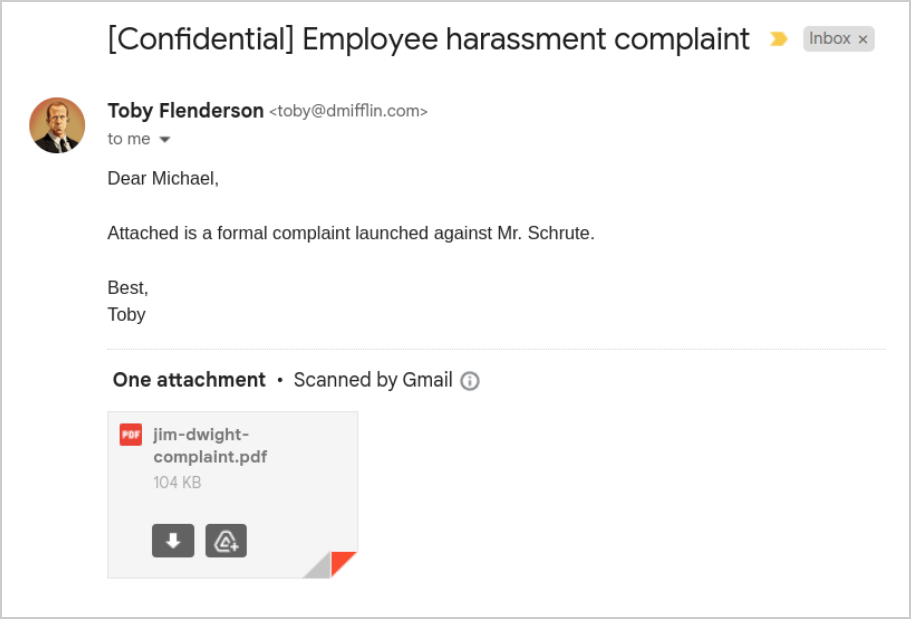
It is a reality that confidential and sensitive information is sent by email every day. This is perceived as safe. Like in the case of Toby, he’s sending a confidential document to a colleague. He’s using the company’s email, and believes that the document is not being shared “outside” of the company. But there are still many questions that need to be addressed. Is the email server run internally, is it outsourced or are they using a SaaS email solution? Who has access to the email servers? Are there backups of the email server? Who has access to the backups? Where are they stored?
Security
As well as addressing the issue of privacy and how sensitive information is stored, we must also consider the fact that email is an important target for threat actors. Email is a common first point of entry that threat actors use to gain a foothold in an organization, often through attacks such as phishing and credential stuffing. Not only is it important for gaining access to accounts linked to the email address, but emails also contain a wealth of information that can be extracted from old messages.
In July 2019, a phishing attack aimed at the Oregon Judicial Department compromised five employee email accounts, exposing personal information of more than 6000 people. The data included names, dates of birth, social security numbers and financial information.
In August 2020, Einstein Healthcare Network identified unauthorized access to employee email accounts. The contents of these email accounts were reviewed and were found to contain patient data, including medical records, diagnoses and social security numbers. The affected individuals filed a class action lawsuit which resulted in a settlement.
In October 2022 STG International’s employees were targeted by a phishing attack, which resulted in unauthorized access to email accounts between October 2022 and January 2021. The information exposed included driver’s license and passport numbers, financial information, social security numbers, payment card information as well as usernames and passwords.
These are just a few examples of the vast number of reported instances of email compromise, but they all demonstrate that simply by gaining access to a handful of email accounts, a threat actor can potentially expose vast amounts of sensitive information.
Sharecurely
Sharecurely addresses this risk by ensuring that no sensitive information ever ends up in emails, only single-use links that allow users to download the sent documents. If a threat actor gains access to such an email, after the document has been sent, it will be useless to him. Furthermore, Sharecurely allows users to add an extra layer of security by enabling two-factor authentication, both in the standalone version and through Jira and Confluence. This ensures that, even if a threat actor is monitoring an email account in real time, he will not be able to access shared documents, without compromising the second factor authentication of the recipient.
Try Sharecurely